Archive
BSides Joint Task Force CTF – Detroit Office – Challenge 64 “Flipping Out”
This was an awesome challenge! One my favorite because it had the right amount of clues, pushed my ability to think through a problem and interpersonal collaboration with fellow InfoSec pros in the Midwest community. This is my first CTF so I don’t have any prior experience with this format and am looking at these challenges with “new eyes”.
The challenge was to find the secrets hidden in a JPEG image file by a rogue agent of the BSides Joint Task Force (BSJTS). The JPEG was named ‘hackers.jpg’ which is from the 1995 movie Hackers.
Based on past challenges from the BSJTF, I knew I needed to do a little recon about the movie. I heard of the movie “Hackers“, and can guess what it’s about, but I never saw it. That being the case, unless they seeded it with false data, Wikipedia is my friend.
In the challenge description there were vague references to the movie characters names, “Acid Burn”, “The Phantom Phreak”, “Cereal Killer”, and “Lord Nikon”. I kept this information in the back of my mind as possible clues for later on to use as passwords, assuming the file contained concealed writing in the form of steganography.
I ran the file through photo forensic tests, inverted the colors with GIMP, as well as a couple other tests. Where I got the best clue of what to do next was with Hex Fiend. With hex editors I look at the beginning and end of files to check for changes. The beginning of the ‘hackers.jpg’ file looked kosher because it contained the proper file header ‘JFIF’ on the first line which indicates it’s a JPEG file format.
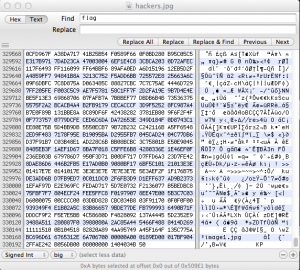
The end of the file had more clues as you can see from the image below.
As you can see from the screenshot, I was searching in the text strings of the file for the word ‘flag’, but I also searched for ‘key’, ‘hacker’, ‘hint’, ‘txt, ‘jpg’ and ‘==’ at different periods during the challenge. ‘jpg’ came up as a search result four times.
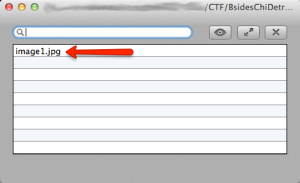
The bottom of the ‘hackers.jpg’ file has a reference to the file named ‘image1.jpg’ which usually (but not always) means another file was embedded inside the ‘hackers.jpg’ file. I opened ‘hackers.jpg, with Ez7z (7zip app for Mac OS X) and saw the following:
Sweet progress! Opening ‘image1.jpg’ revealed this:
Nothing better than a slap in the face when you think you done good. Opening ‘image1.jpg’ in Ez7z and Hex Fiend didn’t result in any discoveries. It looked like stego was the way to go. All tests were a bunch of dead ends. This is where I can say being nice to people and getting to know your fellow community members is important. You never know when you might need a helping hand.
Honorary mention: I met @DrBearSec at BSidesChicago 2013 for the first time. We’ve seen each others tweets on Twitter but that was about it. Since BSidesChicago, we have both been participating in the BSJTF CTF and as a result, we’ve tweeted to each other more frequently. While working on this challenge it was great to bounce ideas off of each other. @DrBearSec has never given me a flag and has acted more like a mentor providing hints. Because of his willingness to be a mentor, I have learned more and never gave up. During this challenge he gave me a hint about the ‘image1.jpg’ file being a red herring and indeed it was. Thank you Bear!
Turning focus back onto the ‘hackers.jpg’ file I ran it through all of the same tests as the ‘image1.jpg’ file. The description for this challenge used the word ‘flip’ twice, plus it’s in the title. Considering the possibility that the bits of the file were flipped, I turned back to Hex Fiend and saw that the last two characters are ‘KP’. ‘PK’ is the file header identifier for the ZIP file format. Now the search was one to flip the bits and open the ZIP file.
I’m not a developer and pretty weak at scripting so I had to turn to the web for help. I found a Python script that reads a file and flips the last line to the beginning of the file. The results were less than optimal. Hex Fiend showed the file header as
00 01 89 ED 00 01 7B F9 04 2F FA E2 42 B0 56 DB 00 08 00 00 00 14 04 03 4B 50 âÌ {˘ /˙‚B∞V€ KP
The letters ‘PK’ are not at the beginning of the file but further inward. It was Memorial Day weekend and I wanted to play with my kids. I got back to the file on Monday night after 11pm central time. The challenge was ending Tuesday morning at 8am central time and there was less than 9 hours left to finish, assuming no sleep. Pressure was on.
Hunting through search results I came across a tool that reverses the bytes of a file. Surprisingly it’s called ‘reverse.exe’. If you aren’t a coder and you like CTFs, you may want to find this tool. ;0)
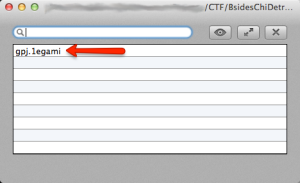
Using a Mac, this means it’s time to fire up a Windows VM to flip the file around. The resulting file I opened with Ez7z and saw this:
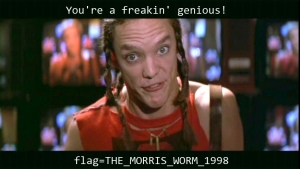
Pay dirt! I like how the name of the image file was also flipped so it wasn’t obviously found when looking at the hex data. When this file was extracted it resulted in this goofy image.
Thank you BSJTF for such a fun and solvable challenge!!